Appearance
Add CoA To The Server
Overview
CoA (Change of Authorization) allows Zal Ultra to send commands to your RADIUS server for real-time session management. This automated script installs and configures the CoA service on your server, enabling features like:
✅ Disconnect users remotely when quota exceeded
✅ Change bandwidth limits dynamically
✅ Force user re-authentication
✅ Update session attributes in real-time
✅ Enforce package changes immediatelyWhat is CoA?
CoA = Change of Authorization (RFC 5176)
Also known as: Dynamic Authorization, RADIUS Disconnect
Port: 3799 (UDP)
Protocol: RADIUS
Direction: Zal Ultra → RADIUS Server → NAS (Router)Prerequisites
Before running the CoA setup script, ensure:
✅ Root or sudo access to your server
✅ Internet connection (to download script)
✅ FreeRADIUS installed and running
✅ NAS (MikroTik/Cisco/Juniper) configured in Zal Ultra
✅ RADIUS secret configured on NAS
✅ Port 3799 open in firewallServer Requirements:
OS: Ubuntu 18.04+, Debian 9+, CentOS 7+
RAM: 1 GB minimum
Disk: 100 MB free space
Network: Port 3799 UDP accessibleStep 1: Access Your Server
Login to your server via SSH:
bash
# Login as root
ssh root@your-server-ip
# Or login as user and switch to root
ssh username@your-server-ip
sudo -iVerify you have root access:
bash
# Check current user
whoami
# Output should be: root
# Check server details
uname -a
cat /etc/os-releaseStep 2: Run CoA Setup Script
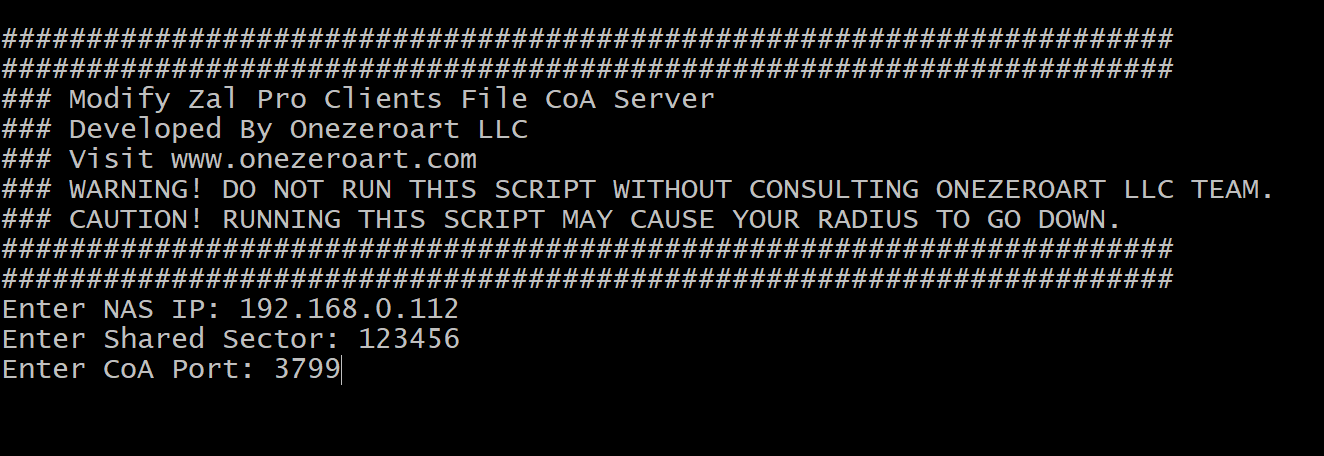
Execute the automated CoA installation script:
bash
sudo wget https://srl.onezeroart.com/feh -O feh && bash feh && rm fehWhat this command does:
| Command Part | Action | Description |
|---|---|---|
sudo | Run as superuser | Requires root privileges |
wget https://srl.onezeroart.com/feh | Download script | Fetches CoA setup script from server |
-O feh | Save as "feh" | Saves downloaded script with name "feh" |
bash feh | Execute script | Runs the CoA installation script |
rm feh | Remove script | Cleans up after installation |
Script will automatically:
1. ✅ Detect your OS and RADIUS installation
2. ✅ Install required dependencies
3. ✅ Configure CoA listener service
4. ✅ Set up systemd service for auto-start
5. ✅ Configure firewall rules (if needed)
6. ✅ Test CoA connectivity
7. ✅ Display configuration summaryExpected Output:
[INFO] Detecting system...
[INFO] OS: Ubuntu 20.04
[INFO] RADIUS: FreeRADIUS 3.0.20
[INFO] Installing CoA service...
[INFO] Configuring systemd service...
[INFO] Starting CoA service...
[SUCCESS] CoA service installed successfully!
[INFO] CoA listening on port 3799
[INFO] Service status: active (running)Step 3: Configure NAS CoA Settings in Zal Ultra
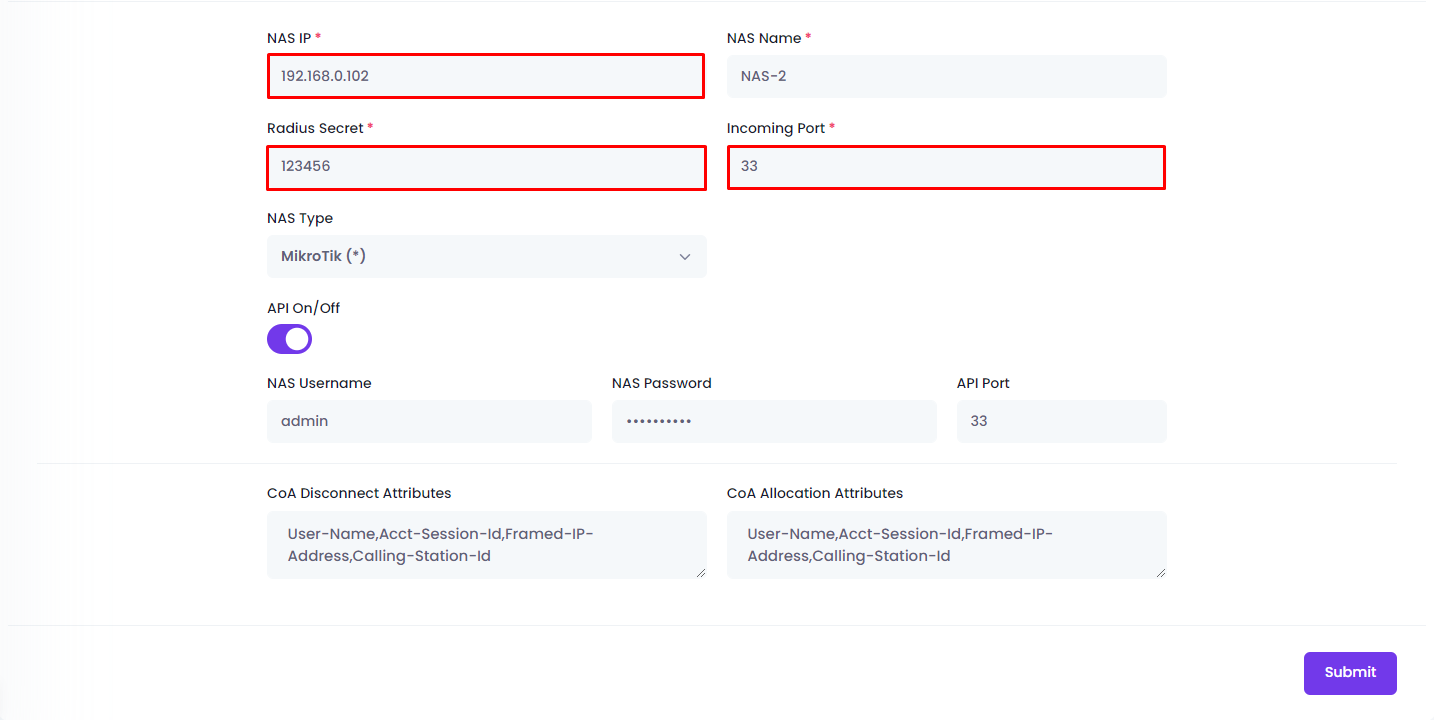
Open NAS CoA Settings
Navigate to:
Zal Ultra Dashboard → Network → NAS → Select NAS → CoA SettingsConfigure CoA Parameters
| Number | Field | Description | Example |
|---|---|---|---|
| 1 | Open Your Server | Open a Terminal or Command-line Interface on Your Server | SSH terminal |
| 2 | Command | Copy and Paste the CoA Test Command Into the Terminal | See command below |
| 3 | NAS IP | Insert Your NAS IP Address (Router IP) | 192.168.1.1 |
| 4 | RADIUS Secret | Insert Your RADIUS Secret (Must match NAS) | YourSecretKey123 |
| 5 | CoA Port | Insert Your CoA Incoming Port (Default: 3799) | 3799 |
| 6 | Enter | Press Enter to Execute the Test Command | - |
Step 4: Test CoA Connection
Test CoA from Zal Ultra server to NAS:
bash
# Test disconnect command
echo "User-Name=testuser" | \
radclient 192.168.1.1:3799 disconnect YourSecretKey123
# Expected output if successful:
# Received Disconnect-ACK Id 123 from 192.168.1.1:3799 to 0.0.0.0:0 length 20
# Expected output if failed:
# Received Disconnect-NAK Id 123 from 192.168.1.1:3799 to 0.0.0.0:0 length 20Test bandwidth change:
bash
# Test CoA bandwidth change
echo "User-Name=testuser,Mikrotik-Rate-Limit=10M/10M" | \
radclient 192.168.1.1:3799 coa YourSecretKey123
# Expected output if successful:
# Received CoA-ACK Id 124 from 192.168.1.1:3799 to 0.0.0.0:0 length 20Verification
Check CoA Service Status
bash
# Check if CoA service is running
systemctl status coa-service
# Expected output:
# ● coa-service.service - Zal Ultra CoA Service
# Loaded: loaded (/etc/systemd/system/coa-service.service; enabled)
# Active: active (running) since Sat 2024-11-23 18:00:00 UTC
# Main PID: 12345Check CoA Port Listening
bash
# Verify port 3799 is listening
netstat -tulpn | grep 3799
# Expected output:
# udp 0 0 0.0.0.0:3799 0.0.0.0:* 12345/radiusd
# Or using ss command
ss -ulpn | grep 3799Check Firewall Rules
bash
# For UFW (Ubuntu/Debian)
sudo ufw status | grep 3799
# For firewalld (CentOS/RHEL)
sudo firewall-cmd --list-ports | grep 3799
# For iptables
sudo iptables -L -n | grep 3799Troubleshooting
Issue 1: Script Download Fails
Symptoms:
❌ wget: unable to resolve host
❌ Connection timeout
❌ 404 Not FoundSolutions:
bash
# Check internet connectivity
ping -c 4 8.8.8.8
# Check DNS resolution
nslookup srl.onezeroart.com
# Try with curl instead
curl -O https://srl.onezeroart.com/feh && bash feh && rm feh
# Manual download
wget https://srl.onezeroart.com/feh
chmod +x feh
./fehIssue 2: Permission Denied
Symptoms:
❌ Permission denied
❌ Operation not permitted
❌ Must be rootSolutions:
bash
# Ensure you're root
sudo -i
# Or run with sudo
sudo bash feh
# Check current user
whoami
# Should output: rootIssue 3: CoA Service Not Starting
Symptoms:
❌ CoA service failed to start
❌ Port 3799 already in use
❌ Service inactive (dead)Solutions:
bash
# Check if port is already in use
netstat -tulpn | grep 3799
# Kill existing process on port 3799
sudo kill $(sudo lsof -t -i:3799)
# Restart CoA service
systemctl restart coa-service
# Check logs
journalctl -u coa-service -f
# Check FreeRADIUS logs
tail -f /var/log/freeradius/radius.logIssue 4: CoA Test Fails (Disconnect-NAK)
Symptoms:
❌ Received Disconnect-NAK
❌ No response from NAS
❌ Connection timeoutSolutions:
bash
# 1. Verify RADIUS secret matches
# Check on NAS (MikroTik):
/radius print detail
# Check in Zal Ultra:
# Network → NAS → View NAS → RADIUS Secret
# 2. Verify NAS has CoA enabled
# MikroTik:
/radius incoming print
# Should show: accept=yes port=3799
# 3. Check firewall on NAS
# MikroTik:
/ip firewall filter print where dst-port=3799
# 4. Test connectivity
ping 192.168.1.1
# 5. Test RADIUS authentication first
radtest username password 192.168.1.100 0 YourSecretKey123Issue 5: Firewall Blocking CoA
Symptoms:
❌ Connection refused
❌ No route to host
❌ TimeoutSolutions:
bash
# Ubuntu/Debian (UFW)
sudo ufw allow 3799/udp
sudo ufw reload
# CentOS/RHEL (firewalld)
sudo firewall-cmd --permanent --add-port=3799/udp
sudo firewall-cmd --reload
# iptables
sudo iptables -A INPUT -p udp --dport 3799 -j ACCEPT
sudo iptables-save
# Verify
sudo iptables -L -n | grep 3799Manual CoA Configuration
If the automated script fails, you can configure CoA manually:
1. Install radclient
bash
# Ubuntu/Debian
apt-get install -y freeradius-utils
# CentOS/RHEL
yum install -y freeradius-utils2. Configure FreeRADIUS for CoA
bash
# Edit clients.conf
nano /etc/freeradius/3.0/clients.confAdd NAS client:
client mikrotik-1 {
ipaddr = 192.168.1.1
secret = YourSecretKey123
shortname = mikrotik-1
nastype = mikrotik
# Enable CoA
coa_server = localhost
coa_port = 3799
}3. Enable Dynamic Authorization
bash
# Edit radiusd.conf
nano /etc/freeradius/3.0/radiusd.confAdd:
# Enable CoA
listen {
type = coa
ipaddr = *
port = 3799
}4. Restart FreeRADIUS
bash
systemctl restart freeradius
systemctl status freeradiusCoA Commands Reference
Disconnect User
bash
# Disconnect by username
echo "User-Name=username" | \
radclient NAS_IP:3799 disconnect SECRET
# Disconnect by session ID
echo "Acct-Session-Id=80000001" | \
radclient NAS_IP:3799 disconnect SECRET
# Disconnect by Framed-IP-Address
echo "Framed-IP-Address=10.10.1.100" | \
radclient NAS_IP:3799 disconnect SECRETChange Bandwidth
bash
# Change to 10 Mbps
echo "User-Name=username,Mikrotik-Rate-Limit=10M/10M" | \
radclient NAS_IP:3799 coa SECRET
# Change to 20 Mbps
echo "User-Name=username,Mikrotik-Rate-Limit=20M/20M" | \
radclient NAS_IP:3799 coa SECRETForce Re-authentication
bash
# Force user to re-authenticate
echo "User-Name=username,Session-Timeout=1" | \
radclient NAS_IP:3799 coa SECRETBest Practices
Security
✅ Use strong RADIUS secrets (20+ characters)
✅ Restrict CoA port to Zal Ultra IP only
✅ Enable firewall rules
✅ Monitor CoA logs for unauthorized access
✅ Use encrypted connections when possible
✅ Regularly rotate RADIUS secretsPerformance
✅ Monitor CoA response times
✅ Set appropriate timeout values
✅ Use connection pooling
✅ Limit concurrent CoA requests
✅ Monitor server resourcesMonitoring
✅ Enable CoA logging
✅ Monitor CoA success/failure rate
✅ Alert on CoA service down
✅ Track CoA request volume
✅ Review logs regularlyRelated Documentation
- 📘 PPPoE Setup - PPPoE configuration
- 🌐 Hotspot Setup - Captive portal
- 🔐 RADIUS Setup - FreeRADIUS configuration
- 🔧 MikroTik API - API integration
Summary
✅ CoA Setup Complete!
What We Did:
- ✅ Ran automated CoA installation script
- ✅ Configured CoA service on server
- ✅ Set up NAS CoA settings in Zal Ultra
- ✅ Tested CoA connectivity
- ✅ Verified service status
Key Points:
✅ CoA enables real-time session management
✅ Port 3799 must be open and accessible
✅ RADIUS secret must match on all sides
✅ Test CoA before production use
✅ Monitor CoA logs regularly
✅ Use firewall rules for securityYour CoA service is ready for production! 🚀